If you joined us last week during the Thursday Night Live Coaching session we held, then you know that I said this blog post would contain EVERYTHING you need to know about Password Cracking for the National Cyber League Games (I mean, it’s also in the title, but I wanted to link to that video, too!).
That being said, let’s make sure that we are all on the same page here with some essential vocabulary I’m going to be using throughout this post.
- Hash/Hashing – in shortest terms, the password is stored in an encryption form known as a hash. This process of one-way encryption that is performed to protect a password in storage is called hashing.
- Dictionary attack – attempting every entry on a pre-made list.
- Hybrid attack – combines dictionary with brute-force by attempting every possible variation of the entries on a pre-made list using common substitution principles or adding leading or trailing numbers, etc.
- Rainbow-tables – uses pre-computed hashes.
- Brute-force – attempting every possible combination of letters, numbers, and characters.
In NCL, you almost never really need to use brute-force password attacks. The most important skill is using the correct wordlist. Now usually, a dictionary attack is sufficient. Occasionally, you will need to use the same wordlist with additional attack parameters to run a hybrid attack.
In my experience, there are only three things you need to know how to do with wordlists the NCL Games.
- Use a pre-made wordlist. (Easy)
- Create your own enumerated wordlist. (Medium)
- Generating a wordlist from a database. (Hard)
As far as password cracking tools go, there are several to choose from. For Windows, I prefer to use Cain. It’s got a nice GUI, but unfortunately won’t always install on all OS without changing the firewall permissions. It will work just fine on a Windows 7 virtual machine which is what I use during the competition. For Kali, I just use Hashcat which comes pre-installed.
For each challenge, I’m going to walk you through a couple of different approaches to the challenge depending on your competencies with a command line interface. As I was not good with command line when I started out, I wanted to make sure I showed an alternative for players who weren’t as comfortable.
Using a Pre-Made Wordlist on Kali
For this challenge, we will use the following hashes from my NCL Coaching Guide:
- (15 pts) 8549137cd494c22ae87eef3e18a46986
- (15 pts) 0f96a320a8c0bf7e3f6d375b0d9d3a4c
- (15 pts) 1a8cb8d148b513dfa1d285077fc4e3fb
- (15 pts) 22a313110bf5b84c0a58eecc27deaa30
- (15 pts) e4fd50109f0e40e8c1a895d8e5c71199
Cyber Skyline (the Game Makers for NCL) like to use the rockyou wordlist. In Kali, this can be found by opening a terminal window and running the command:
cd /usr/share/wordlists
Then use the ls command to see the wordlists available. You should see rockyou.txt.gz. The .gz means the file is in a zip. You can use the command below to unzip the file.
gunzip rockyou.txt.gz
If you use ls again, you should know see it listed as just rockyou.txt.
Now at this point, I like to move this file to my downloads folder so that, in the event of an accidental overwrite, I am only working from a copy rather than the source file. To do so, use the following command:
cp rockyou.txt ../../../root/Downloads/
Note: This assumes you are logged in as the root user on your VM.
Now, create a text file in your Downloads folder and paste each hash on it’s own line. I have saved this file as pwhashfile.txt. Then navigate to your Downloads folder and run the command below:
hashcat -m 0 -a 0 -o hashcatoutput.txt pwhashfile.txt rockyou.txt
Let’s break down that command.
- hashcat is the program you want to run.
- -m 0 tells hashcat to use MD5 as the encryption algorithm.
- -a 0 tells hashcat to use a dictionary attack.
- -o hashcatoutput.txt tell hashcat to output the results to hashcatoutput.txt (you can replace this with your own file name)
- pwhashfile.txt is where I stored my hashes that I wanted to crack.
- rockyou.txt is the wordlist file I wanted to use for this attack. (We copied the file to Downloads for convenience.
In my case, I had an error that I frankly don’t understand, but I googled it and it said to add –force to the end. I did so and it worked fine after.
Once this task is finished (it may take some time) you will see the command prompt again. Once that happens, type the following command to see your results!
cat hashcatoutput.txt
Using a Pre-Made Wordlist on Windows
For this challenge, we will use the hashes from the Kali challenge above.
I recently discovered that Cain is no longer available for download. There are a lot of security issues when you use this program (I mean, you have to disable your Windows Firewall to open the program), but if you use the Wayback Machine archives, it’s still available here. Please DO NOT INSTALL THIS PROGRAM ON YOUR HOST MACHINE. YOU MUST USE IT IN A SECURE VM.
Once you install Cain on your Windows 7 VM, you will have to click the “Cracker” tab. Then, on the left, select the hash type you are working with. In most cases, Cyber Skyline uses MD5 or SHA-1.
Right click the grid on the right and click “Add to list” to add your hashes one at a time. What I like about Cain is that it will not let you enter a hash of an incorrect length. This will help you learn to identify hashes.
Once your hashes are all on the list, highlight the ones you are attempting to crack. Right click and select Dictionary Attack.
Under Files, attach the rockyou wordlist (which you already Googled and downloaded on your VM because you are super smart!). Then under Options, make sure only the first box, As Is (Password), is selected. Then hit start. This will begin the shortest scan.
If this does not work, I recommend checking all of the boxes from top to bottom. Note: when you select Case perms, it will uncheck one of the other boxes. Ignore that. It’s fine. Make sure Case perms is checked. Then hit start. This will take a bit longer.
All results will be shown at the bottom as they are identified, but Cain will also store all found hashes until you empty the memory or delete and entry.
Creating an Enumerated Wordlist on Kali
For this challenge, we will use the following hashes from my NCL Coaching Guide. It appears that they are all in the same format: “SKY-KAIT-” followed by 4 digits.
- (15 points) c38d29e8899455c85ee03d11abbd262b
- (15 points) ff8f9efad5c9f106ac39e5290d810c91
- (15 points) 425206344bd204933a38236b715c498f
- (15 points) ab37c335e51b2855cb5a11ca89041733
- (15 points) 82dcf30f8c7c8d4f23961f7e0c1d3cee
For this, I like to use Crunch Wordlist Generator. The syntax is relatively easy. Just go to command line and type crunch <min> <max> [options]. The options can get tricky, but with a challenge like this, it’s just:
crunch 13 13 -t SKY-KAIT-%%%% -o SKY-KAIT-NUMB.txt
- crunch is the program you want to use.
- 13 is the minimum number of characters I want to use in this list. (don’t forget to count the dashes!)
- 13 is also the maximum number of characters I want to use in this list.
- -t says I want to use a pattern.
- SKY-KAIT-%%%% is the pattern I want to use. % is a substitute character for any number.
- -o SKY-KAIT-NUMB.txt tells the program I want to output the results to the file named SKY-KAIT-NUMB.txt.
Now use the directions above to use your wordlist just like you previously used the rockyou wordlist. Should work pretty quickly!
Creating an Enumerated Wordlist on Windows
There may be better ways, but this is a throwback to my VERY first wordlist. We will use the same hashes as the challenge above.
To start, open Excel and create the following text in cell A1.

Now click on that tiny blue box in the bottom, right corner of the cell and drag it down.
Keep dragging.
Keep dragging.
Keep dragging.
Eventually, you should have a list that looks like this:
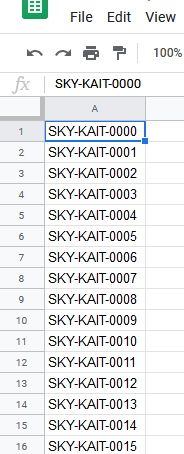
And you will just keep going until you reach SKY-KAIT-9999. Then copy the cells into a notepad file. (Notepad++ also works). Save that as a text file and now you have a wordlist! #throwbacktowhenIdidntknowthings
Creating a Wordlist From a Database
For this challenge, we will use the following hashes from my NCL Coaching Guide. It appears that they are all based off Pokemon.
- (15 points) 3546576a03c2c8229175eede8c02f89
- (15 points) a19d7a52bff83b0e4012d2c766e2f731
- (15 points) 5a31b6b31f92c8f797505ca26af4b9de
- (15 points) 857875c031fce47b2d40be0ce3ffd0bf
- (15 points) dc6054fbe36c8a2bd49b1d05b3b872ee
So for this one, I’m going to remind you that there are plenty of ways to get things done. Really smart people can use web scrappers, etc.
I was not one of those smart people when I first started in NCL. So I used excel. (Anyone else noticing a pattern here? If you are wondering, I love excel, I have always been good at excel, and I firmly believe you should use things you are familiar with.)
So first, I googled Pokemon List and found a wikipedia page with the Gen-1 Pokemon. I put all the data in excel, used text-to-columns. Filtered my data appropriately and then pasted my list of Pokemon types into a Notepad file to save it as a .txt file.
I ran a dictionary attack and got nothing. So I ran a dictionary attack in Cain with the following options checked:
- As Is (Password)
- Reverse (PASSWORD – DROWSSAP)
- Double (Pass – PassPass)
- Lowercase (PASSWORD – password)
- Uppercase (password – PASSWORD)
- Num. sub. perms (Pass, P4ss, Pa5s,…P45s…P455)
- Two number Hybrid Brute (Pass0…Pass99)
This returned one result: Charizard6.
Now, this is where some general nerd knowledge came in handy. 10 year old Kait played a lot of Pokemon Yellow on her Gameboy Color and knew that Charizard was the 6th Pokemon. It had a Pokedex (Pokemon Index) number of 6. So I went back to the spreadsheet and added a second column to my reference sheet. Then ran a standard dictionary attack.
Sure enough, all the passwords were Pokemon plus their Pokedex number.
While not all database password cracking challenges are this easy, you should have enough foundational knowledge to do fairly well. I fully expect you to get all the answers for the Easy and Medium challenges from this guide alone!
That being said, have a great season and happy hacking.

Thanks!!!! So informative and I can’t to try it out 😊
LikeLiked by 1 person
Let me know how it goes!
LikeLike
Where is the link to the video for the password cracking session?
LikeLike
how do i run a command in the download files on kali to run hashcat? I’m on “using a pre-made wordlist on kali” and stuck after making a rockyou.txt and a pwhash.txt file.
LikeLike
Nevermind i figured it out. Cool tutorial I’m learning so much with these guides!
LikeLike
Hi Kait,
Thanks for all the great info you’ve given. It’s been very helpful. I have found that, at least for the easier hashed password challenges, using https://crackstation.net/ is a time saver. Haven’t used it on harder challenges yet, so I can’t comment on how well it works there.
Anyway, keep up the great work.
LikeLike
Hi Kait,
Can you show how your wordlist looks like after adding a column with pokemon numbers? Thanks. Mark
LikeLike
Hi, after hitting ‘hashcat -m 0 -a 0 -o hashcatoutput.txt pwhashfile.txt rockyou.txt’, I get an error message saying “Illegal Instruction”. Do you have any idea what I am missing?
LikeLike
Hi, Nicole! Please bring your question to the Cyber Skyline Slack channel: http://cyber-skyline.slack.com/
LikeLike