Introduction
With a username like CryptoKait, I figure it’s about time that I write my own “Introduction to Cryptography Guide.”
Well, that and Iowa State University’s Women’s Alliance for Cybersecurity student organization invited me to guest lecture this tonight so I should probably attempt to provide some sort of supplemental materials. Maybe. If I can ever get past this writer’s block.
Before we get started, there’s a few things I need to disclose. First of all, I’m not an expert on Cryptography, just an enthusiast. I don’t 100% know if the information in this guide is the industry standard. This is my understanding of the subject. Most of my information here is based on the needed skills for the National Cyber League competition. The following is my own opinions/knowledge/advice based on my own competition experience.
Crypto Basics By Simon Singh
First, let’s cover some basic vocabulary we are going to be using throughout this guide. This info will be taken directly from the Introduction of Simon Singh‘s “The Codebook” which is one of the best books I have ever read. Many parts of this guide should truly thank him. I spent many hours pouring over his website and his book when I first learned about Cryptography.
“Turning to the purists,… the word “code” refers to a very particular type of secret communication… In a code, a word or phrase is replaced with a word, number, or symbol. For example, secret agents have codenames, words that are used instead of their real names in order to masks their identities. Similarly, the phrase Attack at dawn could be replaced by the codeword, Jupiter... The alternative to a code is a cipher, a technique that acts as a more fundamental level, by replacing letters rather than whole words.”
A Short Vocabulary Lesson
Let’s cover some important terms now so we don’t have to explain them later.
Cipher – Encryption one letter at a time.
Code – Encryption by word or phrase.
Plaintext – The readable message.
Ciphertext – The encrypted message.
Encrypt/Encode/Encipher – The process of turning plaintext to ciphertext.
Decrypt/Decode/Decipher – The process of turning ciphertext to plaintext.
Break/Crack – The process of turning ciphertext to plaintext.
Key/Keyword/Key Phrase – The needed information to encrypt or decrypt a cipher.
Protocol – The rules, methods, or standards of the encryption.
The breakdown of Cryptography (the art of secret writing) is made clear by this image from Simon Singh’s book “The Code Book”
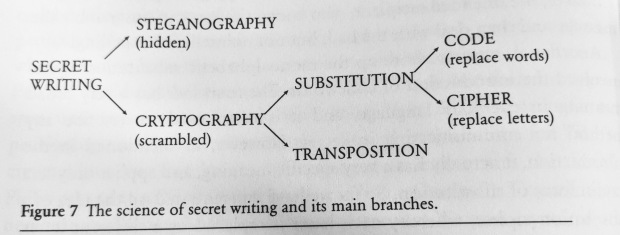
My Crypto Breakdown
I’m going to talk about 3 Categories of Cryptography. Again, I’m not sure how the industry divides them up, but this is how I like to break it down.
First, we will talk about, what I refer to as, “Historical Cryptography”, which are the more traditional methods of Cryptography. Then I’ll cover “Number-Based Cryptography.” I like to talk about this as its own entity because it requires a different mindset than the rest. Due to time, we will not be able to cover what I call “Modern to Quantum Cryptography” which are the present encryption methods and possible futures of Cryptography. I chose to skip this section mostly because it all requires utilities to break and can’t be done by hand (which I find to be much more satisfying).
Historical Cryptography
While there may be more options out there, all the ciphers we will discuss today will fall into one of two categories: Transposition Ciphers and Substitution Ciphers.
Transposition Ciphers are ciphers where all of the letters remain the same, but the letters are rearranged in a complicated or confusing order to encrypt the plaintext. Think of this as the slider puzzle of cryptography- you can’t change the letters, but you can move them all around.
Meanwhile, Substitution Ciphers are ciphers where the letters are substituted or replaced with other letters, numbers, or symbols.
Transposition Ciphers
Transposition Ciphers have a million different options.
Backwards, Upside-Down, Sideways, Bottom-to-Top, Any-Which-Way-You-Want-It
(more info soon) I promise to follow up with an additional blog about the Nancy Drew: Secrets Can Kill computer game and all of the many transposition ciphers that can be found in the game that inspired my interest in Cryptography (and frankly cybersecurity) very soon!
Columnar
The shortest definition of this type of cipher is when the message is written on a grid and then the columns are rearranged according to a key. Rumkin (one of my favorite cryptography tools) has the following example on their site:
To encode the message: “Which wristwatches are Swiss wristwatches” using the KEY: “42531”, the letters are written (without spaces; in all caps) across the grid that has 5 columns (one for each of the numbers in the key). When you reach the end of the column, continue to the next line indefinitely until your message is fully written out.
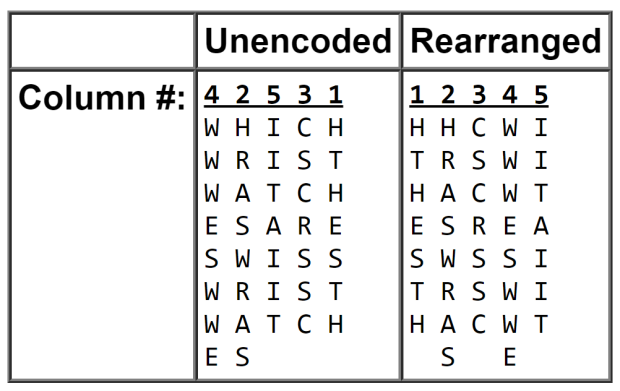
Then, as you can see in the image above, rearrange the columns so that the header or key number is written ascendingly (or descending if that is your established protocol).
To write the now encrypted message, you can just simply write the letters as they read across each row with spaces wherever you see fit.
For example: HHC WITR SWIH ACW TESREA SWSS ITRSW IHA CWTSE.
Railfence
This cipher, named for its appearance that resembles the top of a white picket fence, is also featured on Rumkin. For this example, we will use the secret message of “WAFFLES FOR BREAKFAST” and a key of “3”.
Example 1
To encrypt this message, write the message on a sort of “wave” manner, as featured below, going from left to right, and going down and then up “3” rows. The “*” character represents spaces. Then, much like the columnar cipher above, you will write the message across each row to encrypt.
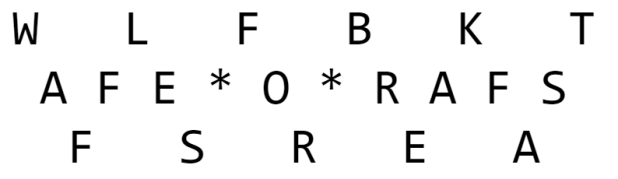
The ciphertext will now be the letters as you read them across the rows like you would read a book. It will look like:
WLFBKT
AFE O RAFS
FSREA
You can also just combine the lines to make it more illegible:
“WLFBKTAFE O RAFSFSREA”
Example 2
For this type of cipher, you can adjust the number of “rails.” To encrypt “This is my secret message!” with a key of “5”, write the letters as featured below (blue asterisks for spaces):
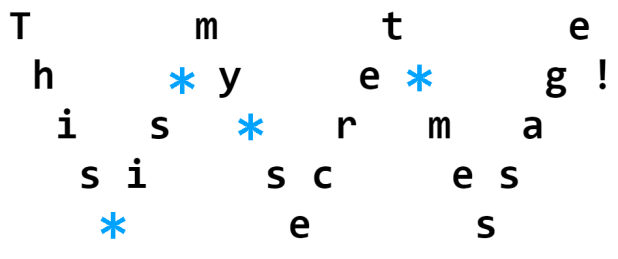
The ciphertext would read as “TMTEH YE G!IS RMASISCES ES”. Pretty tough to unscramble if you don’t know the protocol, huh?
Substitution Ciphers
We are going to discuss 4 main types of substitution ciphers today: Shift Cipher, Morse Code, Atbash, Symbolic Substitution, (my personal favorite) the Vingenere Cipher, and Numeric-based Cryptography.
Shift Cipher
Famously used by Julius Caesar as the first documented use of substation ciphers for military purposes; this cipher is commonly referred to as Caesar’s Cipher or ROT (rotation) Cipher. It shifts or rotates the alphabet a set number of places. For example, Caesar’s famous use was the ROT-3 (rotate 3).
In a ROT-3, each letter would be shifted down 3 places in the alphabet. “A” would become “D”, “B” would become “E”, etc. See below:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
becomes
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
So the plaintext message: attack at dawn
becomes the ciphertext: dwwdfn dw gdzq
This can work with any “ROT” 1-25. Why only 1-25? A ROT-26 would create the original alphabet with no change. Anything higher would be the same as that number minus 26. For example, a ROT-125 would be the same as a ROT-99, ROT-73, ROT- 47, and ROT-21. For simplicity sake, it’s just easier to stick with 1-25.
To decrypt a shift cipher, you only need to rotate the alphabet again (26 – the original key). So to decrypt a ROT-3, you rotate the cipher ROT-23. A ROT-13 is a very unique case. A ROT-13 uses the same encryption and decryption algorithm. This is VERY common in the National Cyber League Competition. When trying what I suspect is a shift cipher, I usually start with ROT-13 before anything else.
Morse Code
I won’t go too in-depth here for brevity sake. Invented by Samuel Morse, this lettering system uses dots and dashes to transmit messages. Commonly used letter were given short codes; less commonly used letters were given the longer codes.
This is one of the few ciphers that can be implemented both written and as an auditory cipher.

Atbash Cipher
Another favorite of mine, this simply uses a reversed alphabet! While the long version of the key is:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
becomes
Z Y X W V U T S R Q P O N M L K J I H G F E D C B A
I use a half key because when you get to M, you can just continue on the bottom row from right to left (almost like a wrap-around).
A B C D E F G H I J K L M
Z Y X W V U T S R Q P O N
Both will work, but for fast notes in class (not that I would ever do this), the halved alphabet is more efficient.
Symbolic Substitution
This encryption type simply uses symbols instead of letters. It usually requires a key.
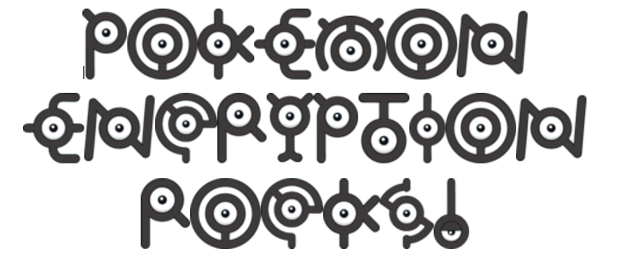
Unown Pokemon
One of the most famous millennial versions of the Symbolic Substitution Cipher is the Unown Pokemon. They are relatively easy to read since the Pokemon looks like the letter of the alphabet they represent. Plus, this is a pretty cute encryption type.
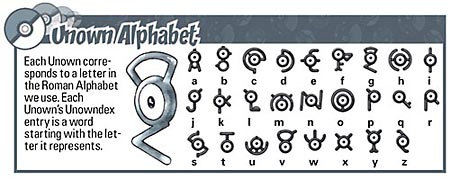
The example below reads: “Pokemon Encryption Rocks!”
Aurebesh
If Millennial references aren’t your speed, there are famous symbolic encryption types for 80s babies, too! If you prefer Millennial Falcon over Pokemon, this encryption type is meant for you!
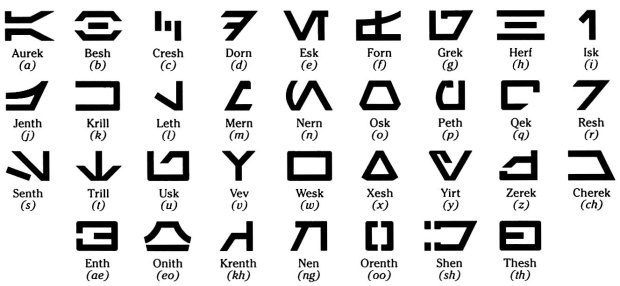
“The Aurebesh is a lot like Boba Fett—it is a facet of the Star Wars phenomenon that had its origin as a cinematic aside, but which has come to be widely embraced, far out of proportion to its humble origins.”
―Stephen Crane
An example of this cipher is: I find your lack of faith disturbing. (see below)
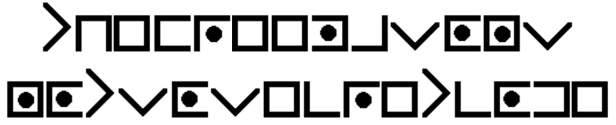
PigPen (Freemason Cipher)
And if that is somehow still just too current for you, Symbolic Cryptography goes wayyyyyyyyy back to the early 18th century. Pigpen was used so frequently by the Freemasons that it became known as the “Freemason Cipher”. It had an interesting key that was designed to be pictured in the mind’s eye so as to never have to write it down. They key looks like this:
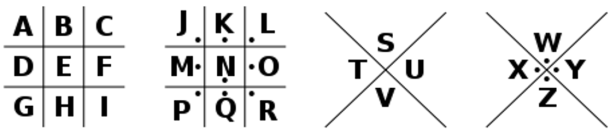
It can be translated by looking at the lines that touch each letter. A substitution alphabet is shown below.
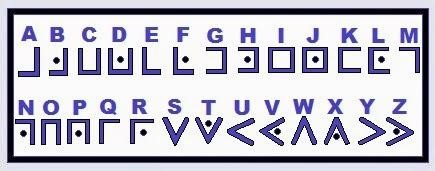
Below is the secret message “the Freemasons’ not so secret code!”
Vingenere
This is actually my favorite cipher! Unlike the previous substitution ciphers in which each letter will always translate to the same letter, number, or symbol (which is known as a monoalphabetic substitution), the Vigenere cipher uses several encryption alphabets and switches between them!
It requires a secret word or phrase. Let’s use “SECRET”.
Let’s have our plaintext be: ONE LAST CIPHER
| O | N | E | L | A | S | T | C | I | P | H | E | R |
| S | E | C | R | E | T | S | E | C | R | E | T | S |
Using a table like the one above, in the first row, write the letters of your plaintext. On the second row, write your secret word as many times as you need to in order to fill up every space. Then use the chart below. Where the two letters in the same column on the table above intersect will be equivalent ciphertext letter.
| O | N | E | L | A | S | T | C | I | P | H | E | R |
| S | E | C | R | E | T | S | E | C | R | E | T | S |
| G | R | G | C | E | L | L | G | K | G | L | X | J |
One of the unique features of the Vingenere cipher is that the same letter can translate to different letters depending on its’ position. For example, there is an “e” in “one” and “cipher”. The “e” in “one” becomes “G” and the “e” in “cipher” becomes “X“. This is because they are encrypted using different letters of the keyword in row 2.
Numeric-Based Cryptography
While Numeric-Based Cryptography falls under a substitution cipher (in most cases), I feel that it has enough content for its’ own blog post. You can start your journey here.
Wrapping It All Up
If you have questions, suggestions, or want to schedule to have me present on this topic to your group, please use the contact page of my site. Additionally, if you want to test your skills, you can post a ciphertext from one of the methods above in the comments below. Let me know what you think and what you want to see more of!
Happy Hacking!

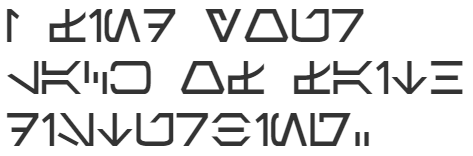
Reblogged this on whitehatHACKR and commented:
What a thorough how-to on ciphers and codes! CryptoKait has made me want to grab an old notebook and write up some secret messages!
LikeLiked by 2 people
Great Intro to Crypto Kait! My students will love this and find it useful both in class (Crypto chapters) and for the NCL games! Thanks again, Dr. Roberrrrrrrrrto
LikeLiked by 1 person
I like looking through a post that can make men and women think. Also, thanks for allowing me to comment!
LikeLiked by 1 person
Hmm is anyone else experiencing problems with the images on this blog loading?
I’m trying to determine if its a problem on my end or if
it’s the blog. Any feed-back would be greatly appreciated.
LikeLiked by 1 person
Not having any problems on my end, could be slow WiFi or you could try switching/updating your browser
LikeLike
Hi CryptoKait!
I am new to the NCL this year, and finally feel like I found my true calling. Thank you for everything you do. Without you, I would be lost. I could use a little more guidance if there is a better way for me to contact you with questions.
Thank you again for everything you do!
Angela Abendroth (Root007)
aabendroth001@my.wilmu.edu
LikeLike